Group uses custom Felismus malware and has a particular interest in South American foreign policy.
By: Symantec Security Response
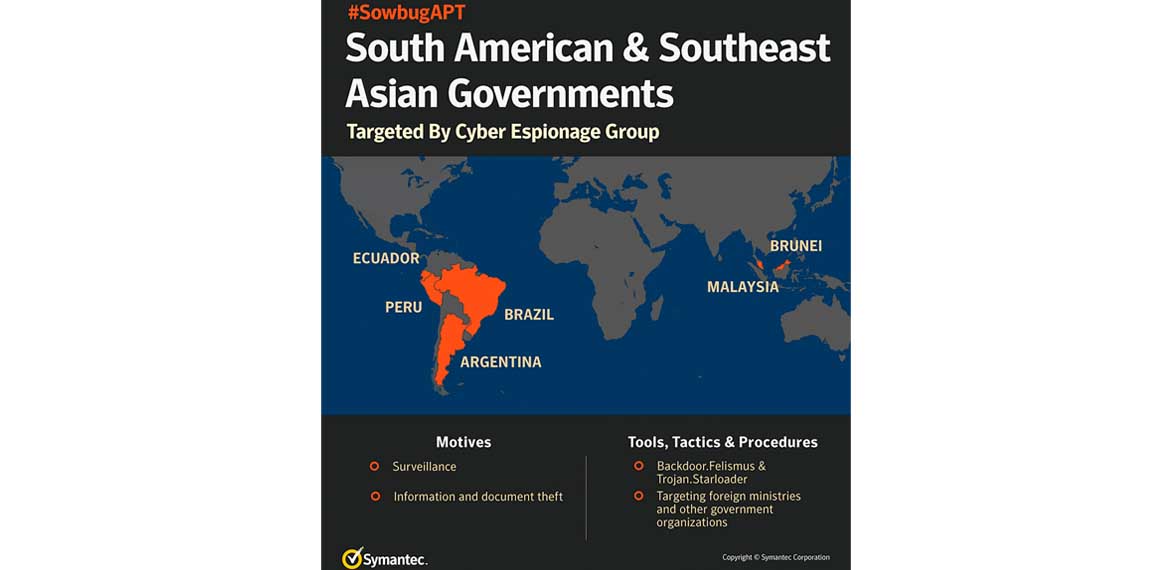
Symantec has identified a previously unknown group called Sowbug that has been conducting highly targeted cyber attacks against organizations in South America and Southeast Asia and appears to be heavily focused on foreign policy institutions and diplomatic targets. Sowbug has been seen mounting classic espionage attacks by stealing documents from the organizations it infiltrates.
Symantec saw the first evidence of Sowbug-related activity with the discovery in March 2017 of an entirely new piece of malware called Felismus used against a target in Southeast Asia. We have subsequently identified further victims on both sides of the Pacific Ocean. While the Felismus tool was first identified in March of this year, its association with Sowbug was unknown until now. Symantec has also been able to connect earlier attack campaigns with Sowbug, demonstrating that it has been active since at least early-2015 and may have been operating even earlier.
To date, Sowbug appears to be focused mainly on government entities in South America and Southeast Asia and has infiltrated organizations in Argentina, Brazil, Ecuador, Peru, Brunei and Malaysia. The group is well resourced, capable of infiltrating multiple targets simultaneously and will often operate outside the working hours of targeted organizations in order to maintain a low profile.
Highly targeted intrusions
Some clues about the motivation and interests of the attackers can be found in their activities after compromising victims. For example, in a 2015 attack on one South American foreign ministry, the group appeared to be searching for very specific information.
The first evidence of its intrusion dated from May 6, 2015 but activity appeared to have begun in earnest on May 12. The attackers appeared to be interested in one division of the ministry that is responsible for relations with the Asia-Pacific region. They attempted to extract all Word documents stored on a file server belonging to this division by bundling them into a RAR archive by running the following command:
cmd.exe /c c:\windows\rar.exe a -m5 -r -ta20150511000000 -v3072 c:\recycler\[REDACTED].rar “\\[REDACTED]\*.docx” \\[REDACTED]\*.doc.
Interestingly, the command specified that only files modified from May 11, 2015 onwards should be archived.
The attackers appear to have successfully extracted the archive because an hour later they returned, this time attempting to extract all documents modified from May 7, 2015, an extra four days’ worth of data. Presumably they either didn’t find what they were looking for in the initial incursion, or else noticed something in the documents they stole earlier that prompted them to hunt for more information.
The attackers didn’t stop there. Their next move was to list any remote shared drives and then attempt to access remote shares owned by the specific government office they were targeting, again attempting to extract all Word documents. In this case, they searched for any documents modified from May 9 onwards. The attackers then seemed to broaden their interest, listing the contents of various directories on remote shares, including one belonging to another division of the South American foreign ministry, this one responsible for relations with international organizations. They also deployed two unknown payloads to the infected server. In total, the attackers maintained a presence on the target’s network for four months between May and September 2015.
CLICK FOR MORE PHOTOS…