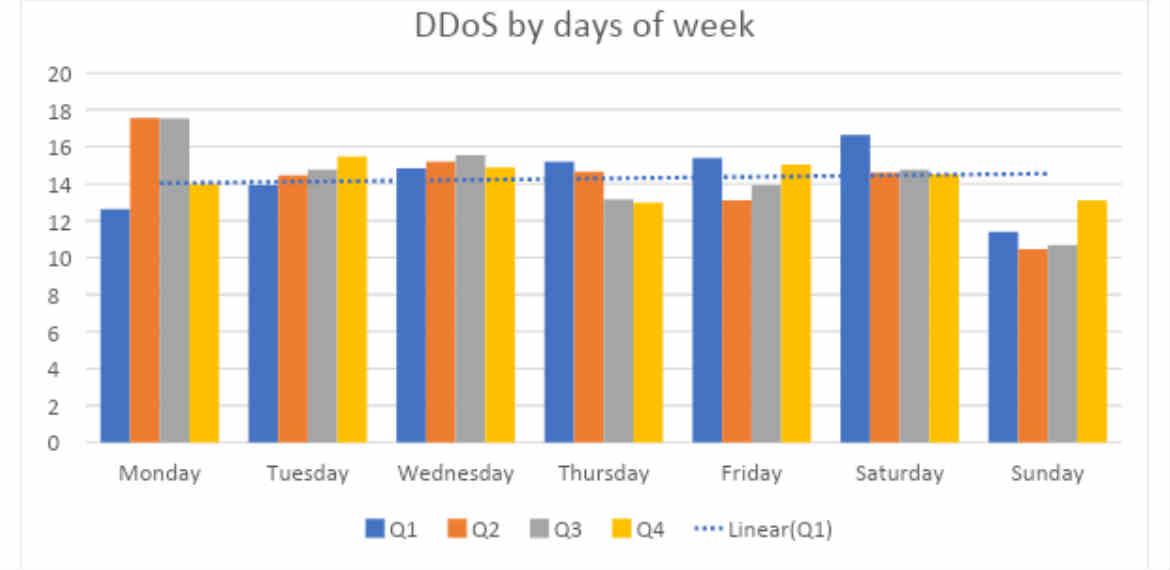
Analysis has revealed that the number of attacks blocked by Kaspersky DDoS Protection in Q4 2018 amounts to only 56% of attacks detected in Q4 2019. Further investigation of botnet activity reveals that around 28% of attacks happened on weekends, with the share of attacks on Sundays growing by two and a half percentage points – reaching 13%. These are findings from the Kaspersky Q4 2019 DDoS attacks report.
In Q4 2019, there were several large-scale DDoS attacks, including ones against financial institutions in South Africa, Singapore and Scandinavian countries. These cyberattacks were also targeted at the Labour party in the United Kingdom as an attempt to disrupt its digital systems, as well as against Minecraft servers set up in the Vatican. This demonstrates that DDoS is still a common attack method amongst cybercriminals seeking financial gain or driven by ideological motives, so organizations should be prepared for such attacks and understand how they evolve.
The report highlights that the main trend during the last quarter of 2019 was increased botnet activity on Sundays. While the growth may seem relatively small (two and a half percentage points), the share of DDoS attacks on this particular day of the week had otherwise been the lowest, and consistent, throughout the rest of the year (around 11% of attacks in Q1 and Q3, and 10% in Q2).
In Q4, Thursday turned out to be the day with the least DDoS activity. In general, attacks became more evenly distributed over a week. Analysis shows that the difference between the most active and the calmest day was only about two and a half percentage points (in the previous quarter, the figure was seven percentage points).
Although the number of DDoS attacks detected by Kaspersky DDoS Protection has grown significantly compared to the same period of 2018, the growth in comparison to Q3 2019 is only marginal (attacks in Q3 2019 equate to 92% of Q4 2019).
There was a more notable rise in so-called smart DDoS attacks, focusing on the application layer and carried out by skilled malefactors (as attacks in Q3 2019 were 73% of those in Q4 2019). Such an increase was quite predictable, since November to December is traditionally a popular time for online business and retail activity. However, Kaspersky experts did not identify a spike on Black Friday or Christmas holiday sales days.
“Despite the significant growth in general, the season turned out to be quieter than expected. We suggest that we didn’t see a storm of attacks on certain days because companies expand their activity to engage with customers for the entirety of the holiday period. So, there is no need for cybercriminals to launch an attack to coincide with a specific event. However, attackers can still find a way to spoil your leisure time, as cybercrime is not an ordinary nine-to-five job, so it is important to ensure that your DDoS prevention solution can automatically protect your web assets,” comments Alexey Kiselev, Business Development Manager on the Kaspersky DDoS Protection team.
To help organizations protect themselves from DDoS attacks on weekends and during popular times of year, Kaspersky recommends taking the following steps:
• Conduct stress tests and web application audits with internal employees or with the help of outsourced specialists, to identify the weakest points in company infrastructure
• Assign specialists responsible for maintaining web resources operations. Ensure they know how to act in case of DDoS attacks and are ready to respond outside of their scheduled working hours
• Verify third-party agreements and contact information. This includes arrangements with an internet service provider, so that you can quickly reach it in case of an attack
• Implement professional solutions to protect the organization against attacks. For example, Kaspersky DDoS Protection combines Kaspersky’s extensive expertise in combating cyberthreats and the company’s unique in-house developments. The solution protects organizations against all types of DDoS attacks regardless of when they happen
Read the full report on Securelist.