Widescale shift towards malicious WSF attachments
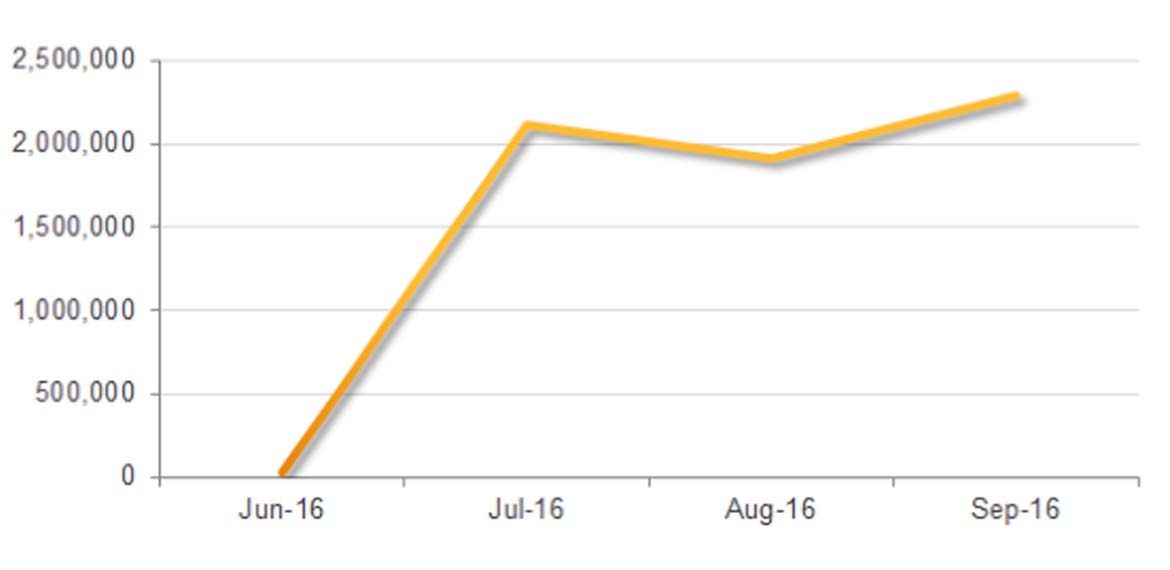
These recent Locky campaigns are part of a broader trend. Over the past number of months, Symantec has noticed a significant increase in the overall numbers of emails being blocked containing malicious WSF attachments. From just over 22,000 in June, the figure shot up to more than 2 million in July. September was a record month, with more than 2.2 million emails blocked.
Figure 2. Number of blocked emails containing malicious WSF attachments by month
Change of tactics
Groups who spread malware through spam campaigns frequently change the format of the malicious attachments used. As security vendors improve their defenses against certain malicious file types, attack groups will switch to alternatives in the hope that more emails will slip through defenses.
For example, Locky spam campaigns are sent by an affiliate that is also used by the Dridex group. The spamming operation had previously used attached Word documents containing a malicious macro (W97M.Downloader). Earlier this year, it moved to using malicious JavaScript attachments (JS.Downloader). It now appears to have shifted to using WSF files instead of pure JavaScript (also detected as JS.Downloader).
In a constantly shifting threat landscape, organizations need to remain vigilant and aware that threats can come from new and unanticipated sources.
Protection
A full protection stack helps to defend against these attacks, including Symantec Email Security.cloud which can block email-borne threats and Symantec Endpoint Security which can block malware on the endpoint.
Symantec and Norton products protect against malicious WSF files with the following detections:
Antivirus:
Antivirus:
• JS.Downloader
Intrusion prevention system:
• System Infected: JS.Downloader Activity
• System Infected: JS.Downloader Activity 2
• System Infected: JS.Downloader Activity 3
• System Infected: JS.Downloader Activity 4
• System Infected: JS.Downloader Activity 5
• System Infected: JS.Downloader Activity 6
• System Infected: JS.Downloader Activity 7
• System Infected: JS.Downloader Activity 8
• System Infected: JS.Downloader Activity 9
• System Infected: JS.Downloader Activity 10
• System Infected: JS.Downloader Activity 11
• System Infected: JS.Downloader Activity 12
• System Infected: JS.Downloader Activity 13
• System Infected: JS.Downloader Activity 23
• Web Attack: JS.Downloader Download 5
Tips on protecting yourself from ransomware
• Regularly back up any files stored on your computer. If your computer does become infected with ransomware, your files can be restored once the malware has been removed.
• Always keep your security software up to date to protect yourself against any new variants of malware.
• Keep your operating system and other software updated. Software updates will frequently include patches for newly discovered security vulnerabilities that could be exploited by attackers.
• Delete any suspicious-looking emails you receive, especially if they contain links or attachments.
• Be extremely wary of any Microsoft Office email attachment that advises you to enable macros to view its content. Unless you are absolutely sure that this is a genuine email from a trusted source, do not enable macros and instead immediately delete the email.